A primer on WPAD and PAC
Web Proxy Auto-Discovery (WPAD) is a protocol that enables discovery of a URL to a proxy configuration file (e.g. http://wpad.example.com/wpad.dat, or other URLs within the client’s network name/domain) for all connected machines on a network. This is done by means of DHCP or DNS, thereby removing the hassle for manual configuration.
WPAD commonly deploys proxy configuration files based off the Proxy Auto-Config (PAC) standard, originally designed by Netscape for use in their proprietary web browser Netscape Navigator. PAC scripts comprise of a single Javascript function named FindProxyForURL(url, host), which in itself contains other predefined functions and options that can be used when defining rules. Clients on the network will then follow these rules for upstream proxy forwarding of web traffic.
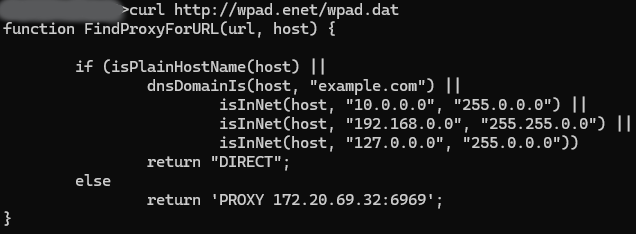
Here's how a PAC script could look like. *Do note that we'll be using this same PAC script when configuring WPAD later on*
function FindProxyForURL(url, host) {
// Traffic headed to 'example.com' and private IP ranges (besides the class B range - 172.16-31.0.0/16)
// aren't forwarded to the proxy below
if (isPlainHostName(host) ||
dnsDomainIs(host, "example.com") ||
isInNet(host, "10.0.0.0", "255.0.0.0") ||
isInNet(host, "192.168.0.0", "255.255.0.0") ||
isInNet(host, "127.0.0.0", "255.0.0.0"))
return "DIRECT";
else
// All other requests will pass through this proxy
return 'PROXY 172.20.69.32:6969';
}
Configuring WPAD with steps
| Machine | IP |
|---|---|
DHCP server (I went with the domain name .enet) |
172.20.69.1 |
Web server (hostname: wpad) |
172.20.69.3 |
| Proxy server | 172.20.69.32 |
| Client | 172.20.69.34 |
A few prerequisites are needed before we can see WPAD in action, they are:
-
A DNS entry on a DNS server or local resolver mapping the
wpadhostname to a web server. -
Said web server serving a PAC script holding the proxy configuration from before. In my case, this file was hosted at
http://wpad.enet/wpad.dat. -
A proxy server listening for upstream proxying of web traffic. I opted for mitmproxy here, but whichever else works too.
-
A WPAD-enabled client on the network. On Windows, enabling the Automatically detect settings option under Settings > Network & Internet > Proxy > Automatic proxy setup (one method of doing so). For Linux on the other hand, setting the
http_proxyorhttps_proxyenvironment variable will usually do the trick, though not all programs check these environment variables. Windows usually fetches the PAC script from a list of WPAD URLs automatically by default whereas Linux doesn’t.
With all that configuration now set up, assuming our client machine has obtained an IP address and the correct domain name from the local DHCP server. We can then monitor the client machine for any DNS queries and HTTP requests made to wpad.enet, which is where the wpad.dat PAC script gets pulled down and applied. These requests are immediately sent to upon enabling automatic proxy discovery on our client machine.
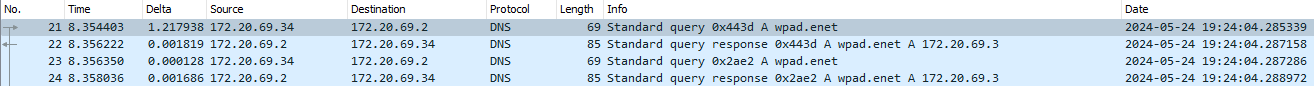
wpad.enet succeed.
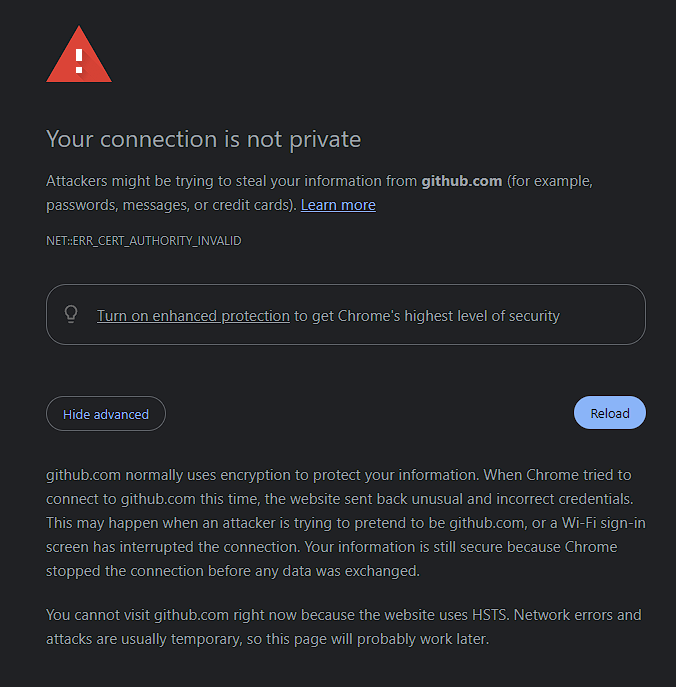
We can now start testing if the rules from our PAC script work as intended. Back on the client machine, I first tested visiting example.com . And as expected, we’re able to reach the landing page without any issues. Visiting github.com on the other hand, made my browser raise a warning prompt prior to loading the page, since traffic has to go through our proxy.
Final thoughts
As you can see, WPAD alongside PAC really makes a sysadmin’s life that much more convenient, especially on large networks with countless machines running on the daily. Just a slight tweak to the machine rollout process and network setup and you’re able to impose your web proxy policies with ease. And of course, this degree of convenience isn’t without its drawbacks, especially in the security department. Given the steps above, an attacker can easily abuse a misconfigured WPAD setup. Thereby forcing victims running e.g. Windows machines (where WPAD is enabled by default) to forward traffic to an attacker-controlled web proxy for MITM sniffing, or spoofing the identity of a legitimate website with hopes of phishing any sensitive data.




